Foundation
OCI: Open Container Initiativefounded by Docker, CoreOS, and othersimage-specruntime-specCRI: Container Runtime Interface enables kubelet to use different runtimesCNI: Container Network Interface
Container Runtimes
high-level runtimes often incorporate low-level runtimes that are otherwise standalone projects.
If tomorrow you get the urge to add your own container project to the ever-growing jungle, you should make it OCI-, CRI- and CNI-compliant

Figure 1: Docker vs. containerd in a Kubernetes context. The dockershim and cri-containerd implementations make the respective APIs CRI-compliant by translating calls back and forth.

Figure 2: containerd allows for the usage of multiple low-level container runtimes, which can be used in Kubernetes interchangeably based on the requirements for a specific application. In this case, Kata is used to run untrusted containers.cri-o
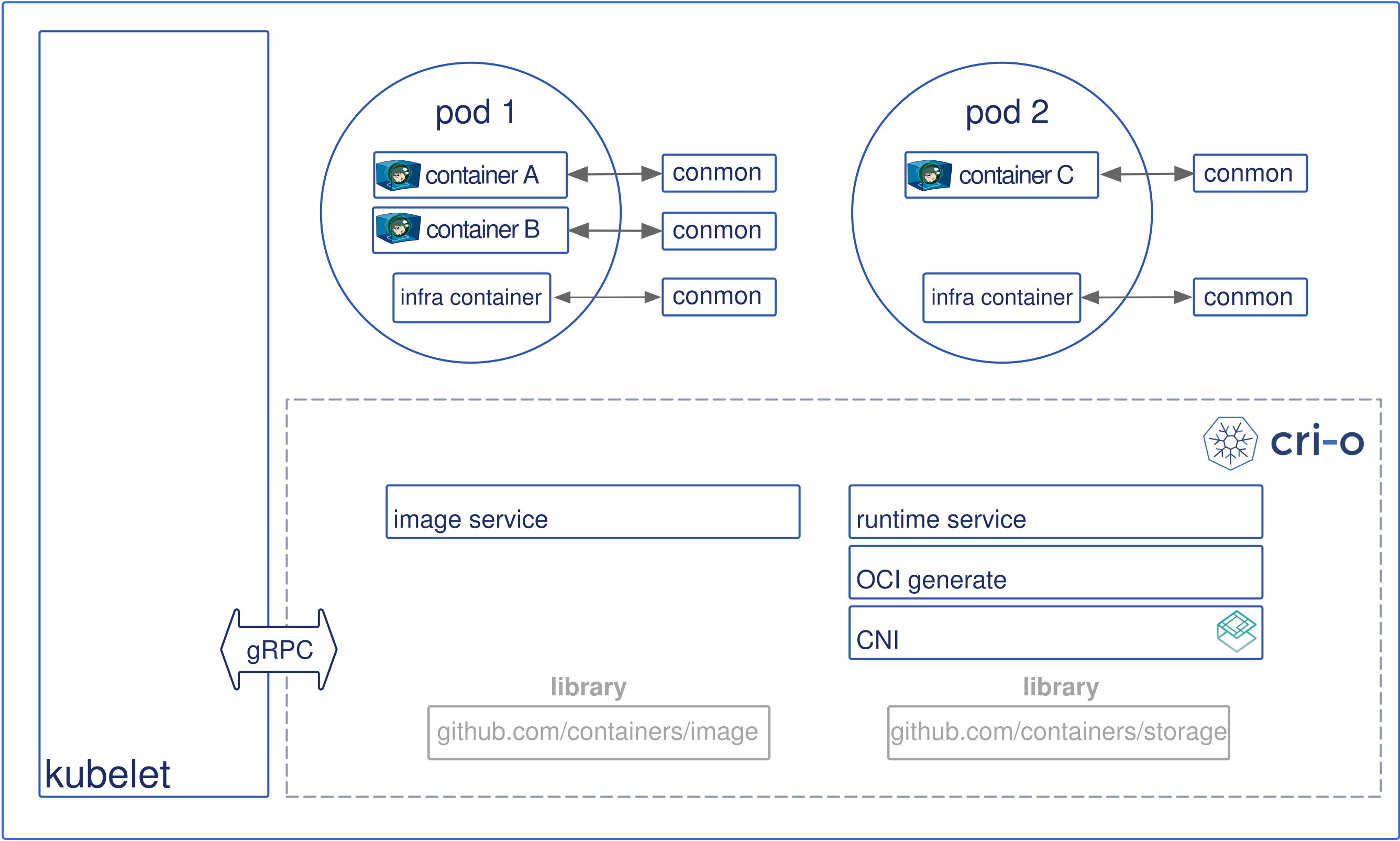
runc = libcontainer + ..runc runs OCI open container image directly(high level) rkt (obsolete) did not rely on daemonlxc: virtual env that does not emulate the hardware. he focus of Linux Containers are base images (e. g. Ubuntu) rather than application-tailored images.singularity focuses on High Performance Computing. Uses Singularity Image Format (SIF), but also supports OCI/CRI
VM-like Container Runtimes
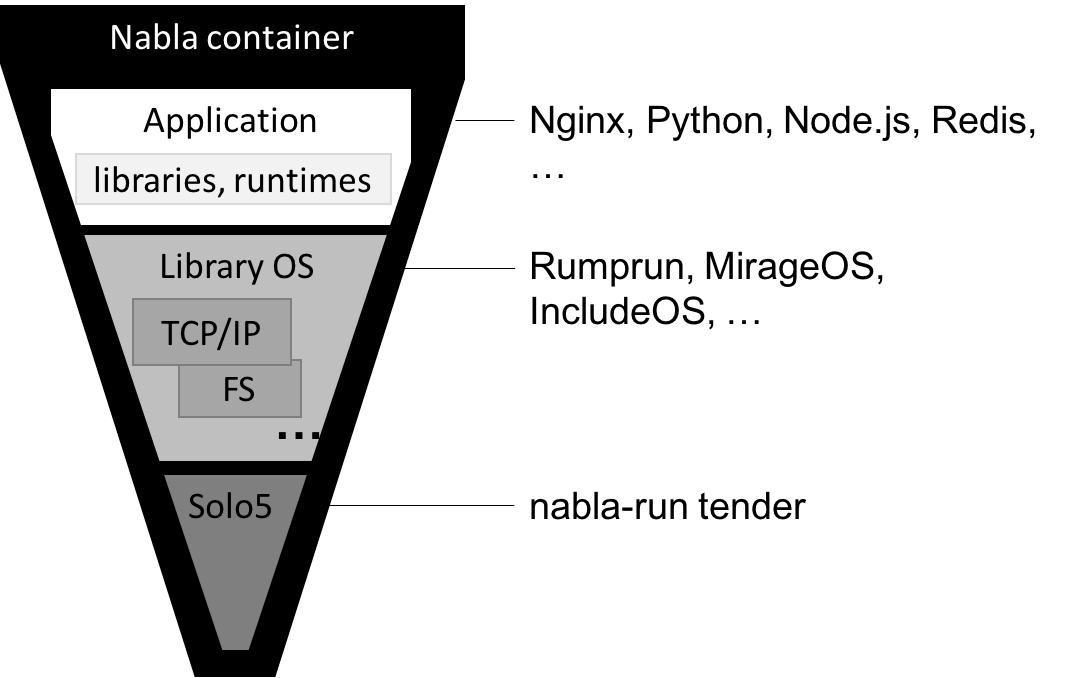
Unikernels only contain the parts of the OS they need and get deployed on top of a hypervisor/VMM. Monitoring and debugging capabilities are very limited. No toolchains officially available.Nabla Container 7 syscalls used, not OCI compliant, CRI compliant (runnc)
Kata ContainersOpenStack project, OCI compilant, CRI compliant, CNI compliant As every container is started inside a new VM (managed by QEMU), Kata provides an optimized base VM image to speed up boot times for them

FirecrackerAmazon project, FaaS, VMM that uses KVM to create microVM.Efforts:
- Firecracker instead of QEMU as VMM for Kata Containers
- firecracker-containerd mapper allows containerd to run containers as microVMs
gVisorGoogle, runsc, OCI compilant, Sentry, GoferSentry is the central user-space OS kernel that the untrusted application uses.Not every system call, /proc or /sys file is implemented.
Source:
and other opensource sites.
